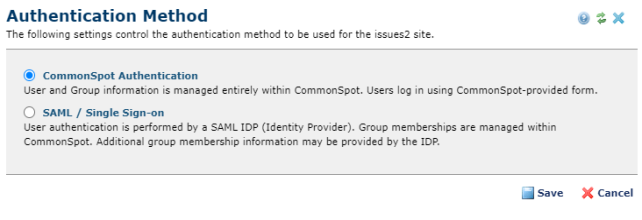
The options in this dialog are to use CommonSpot Authentication, one of the SAML / Single Sign-on options or inherit the SAML configuration from another site on this server that is already configured.

When another site is already configured, the dialog will have the 'Inherit' option.
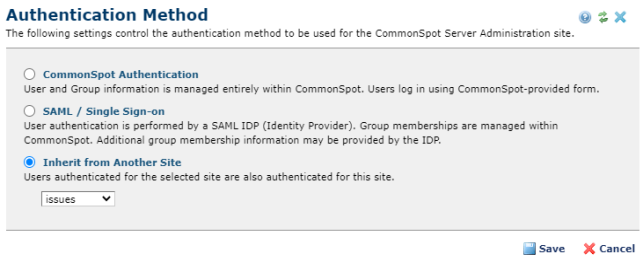
Clicking the Inherit button uses the already configured Authentication method.
Clicking the SAML / Single Sign-on radio button opens the rest of the dialog.
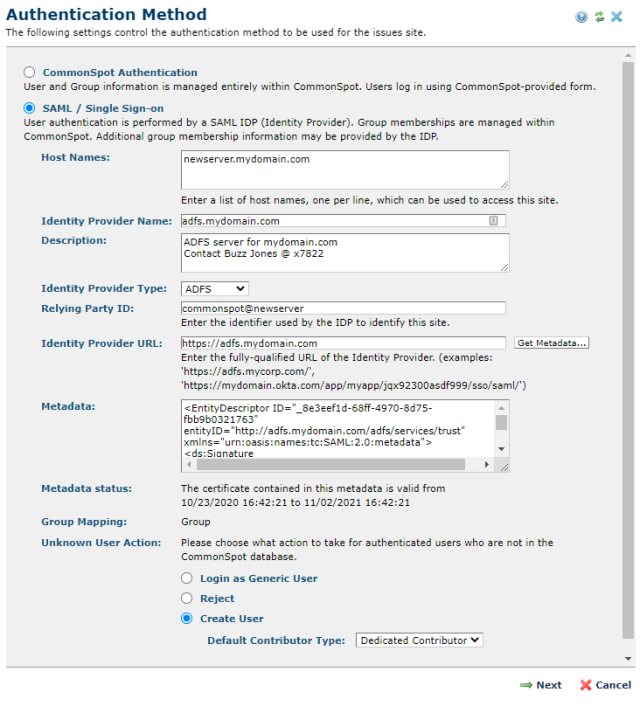
Enter the host names which can be used to access this site, separated by newlines.
Enter the name of the Identity provider.
Enter a brief description of the Identity Provider.
Select ADFS, AWS or Okta, corresponding to the type of the Identity Provider you will be connecting to.
Enter the unique identifier used to identify this instance to the Identity Provider
Enter the URL provided by the identity provider's administrator to get the Identity Provider's metadata, then click the 'Get Metadata..' button to download the metadata. For ADFS servers, this can be just the URL of the Identity Provider.
If you do not have the URL for the Identity Provider's metadata, but instead have been given the metadata XML, paste it here.
Select the action to take when a user who is authenticated by the Identity Provider is unknown to CommonSpot. The available options are:
All users unknown to CommonSpot will share a single CommonSpot account such as 'Generic User' or 'Student'
Users who are unknown to CommonSpot will be denied access
A new CommonSpot account will be created for each new user
Click 'next' to proceed to the next step.
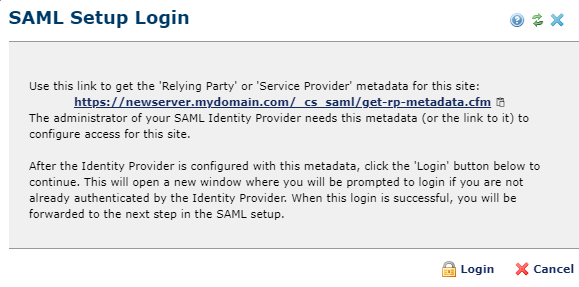
By clicking 'Login', you will be forwarded to the Identity Provider for authentication. The reply from the Identity Provider will allow the configuration to be completed.
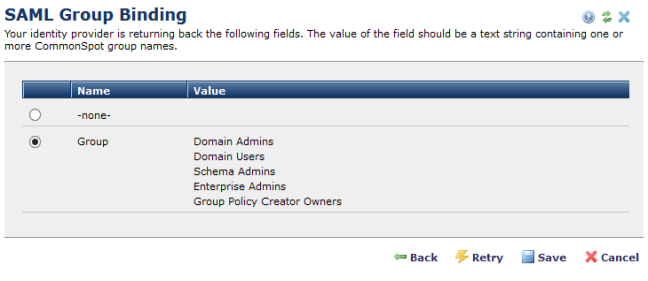
This dialog lists the claims returned by the Identity Provider. If you want to assign CommonSpot permissions according to group memberships returned by the Identity Provider, select the name of the corresponding claim. Otherwise, select '-none-' to manage all group memberships within CommonSpot.
CommonSpot API change
Request.User updates
Several new fields have been added to the 'Request.User' object:
'Refresh SAML Metadata' scheduled task
The metadata for an Identity Provider includes an encryption key which has an expiration date. This metadata needs to be periodically updated to ensure that the most current key is available and to prevent failure of the authentication process due to expiration of this key.
For ADFS and Okta configurations, the Identity Provider provides an URL to get the current metadata, so CommonSpot provides a scheduled job to refresh the locally-stored metadata using this URL.
To configure this scheduled job, use the 'Scheduled Jobs' menu item on the 'Site Administration' page and add a new job using the 'Refresh SAML Metadata' job definition. Consult with the administrator of your Identity Provider to determine an appropriate schedule for this metadata refresh.
For AWS SSO configurations, this metadata will need to be refreshed manually by updating the 'Identity Provider Metadata' field of the 'Authentication' options dialog
ADFS Configuration for use with CommonSpot
The following outlines a simple ADFS configuration using default options. This assumes that the ADFS server is fully configured and ready for establishment of relying party trusts.
Open the 'AD FS Management' application from the 'Administrative Tools' section of the control panel. Select the 'Relying Party Trusts' option in the left-hand column.
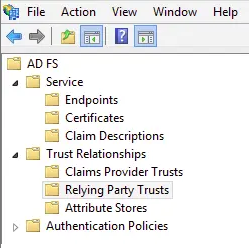
Select 'Add Relying Party Trust...'
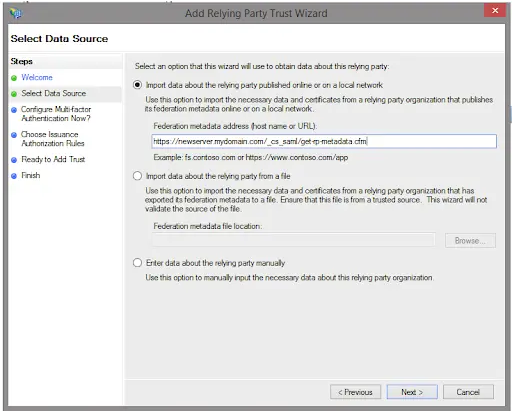
The URL used for the 'Federation metadata address' must use one of the host names listed in the CommonSpot 'Authentication Method' dialog. '_cs_saml/get-rp-metadata.cfm' is the utility to get the 'Relying Party' metadata for the CommonSpot site.
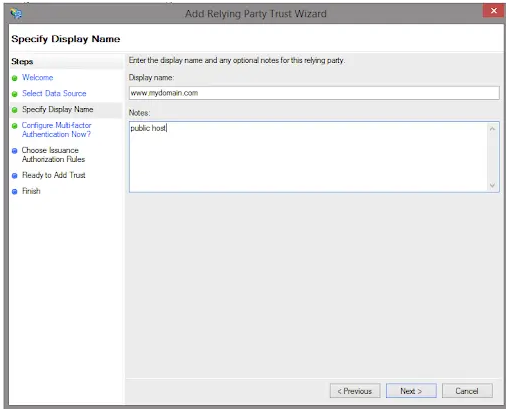
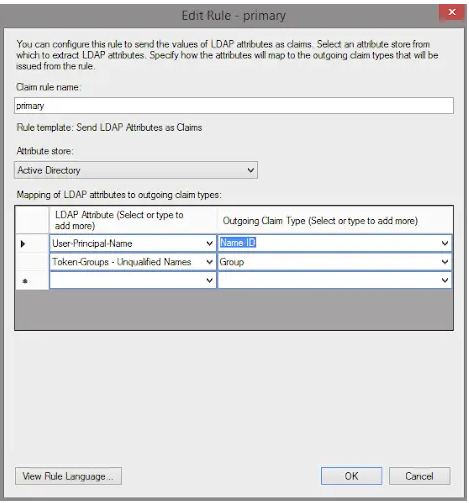
Please note that a 'Name ID' claim must be configured.
If domain groups are to be used with CommonSpot, use either a 'Group' or a 'Role' claim configured to use the 'Token Groups - Unqualified Names' attribute.
Other claims may be added, but will not be directly used by CommonSpot.
When the ADFS configuration is complete for the server, go back to the CommonSpot session and click the 'login' link to proceed to the final step, which is to select which (if any) field is to be used for group membership information.
Related Links
You can download PDF versions of the Content Contributor's, Administrator's, and Elements Reference documents from the support section of paperthin.com (requires login).
For technical support: